Overview
Syllabus
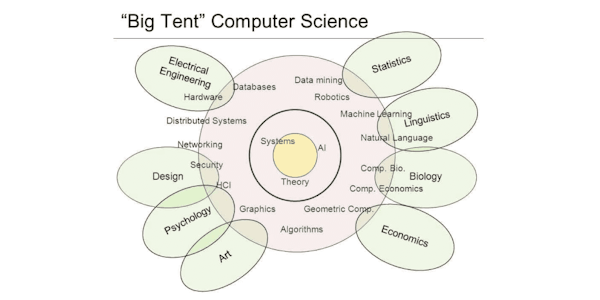
Introduction.
A basic question.
Answer: authenticated encryption.
Constructions Generic composition encrypt-then-MAC key = (kana kmal).
Nonces and associated data.
Many more desirable properties.
Lots of viable constructions.
Implementation mistakes.
Example 1: Apple RNCryptor.v1 [2013].
Why is this a problem?.
Example 2: checksum-MAC (abstract WEP).
The chopchop attack (abstractly).
Signcryption: AE in the pub-key settings [O-RTT mutual authenticated key exchange, for messages] Sender.
A beautiful mistake: iMessage (simplified).
The problem.
Lessons.
Shameless plug ....
Taught by
Stanford Online